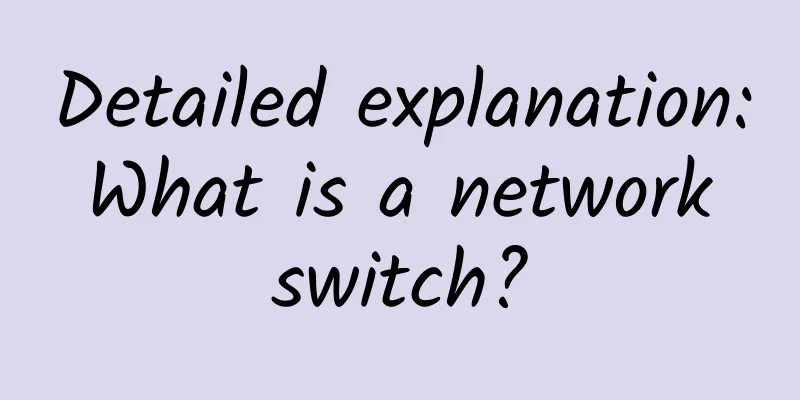
Clarity: Docker's four network modes

|
1. Closed container closed network mode It is equivalent to an isolated island, without communication of network protocol stack In none mode, the Docker container has its own Network Namespace, but no network configuration is performed for the Docker container. In other words, the Docker container has no network card, IP, routing and other information, only the lo network interface. We need to add a network card and configure IP for the Docker container ourselves. The example picture is as follows: 2. Bridged container bridge network mode The network protocol stacks between containers are separated When Docker is started, a docker0 virtual bridge is automatically created on the host, which is actually a Linux bridge and can be understood as a software switch. It forwards traffic between the network ports mounted to it. At the same time, Docker randomly assigns an address in a local unoccupied private network segment (defined in RFC1918) to the docker0 interface. For example, the typical 172.17.42.1, with a mask of 255.255.0.0. The network port in the container started thereafter will also automatically be assigned an address in the same network segment (172.17.0.0/16). When a Docker container is created, a pair of veth pair interfaces are created at the same time (when a data packet is sent to one interface, the other interface can also receive the same data packet). One end of this pair of interfaces is in the container, namely eth0; the other end is locally and mounted to the docker0 bridge, with a name starting with veth (for example, vethAQI2QT). In this way, the host can communicate with the container, and the containers can also communicate with each other. Docker creates a virtual shared network between the host and all containers. As shown in the figure, two containers on the same host communicate through the bridge docker0. (Containers on different hosts need to communicate with each other through the overlay network, which involves some underlying protocols. I will write a separate article to explain it.) 3. Joined container joint mounting network mode Containers can share network protocol stacks, that is, they can communicate through sockets This mode specifies that the newly created container shares a Network Namespace with an existing container instead of sharing it with the host. The newly created container will not create its own network card and configure its own IP, but will share the IP, port range, etc. with a specified container. Similarly, except for the network, the two containers are isolated from other aspects such as the file system and process list. The processes of the two containers can communicate through the lo network card device. The example is as follows: 4. Opentainer container open network mode Share network protocol stack with host The host mode is to specify --network host when starting the container. At this time, the container shares the host's Network Namespace. The port started in the container is directly the host's port. The container will not create a network card and IP, but directly use the host's network card and IP. However, other resources in the container are isolated, such as the file system, users and user groups. Use the host network directly. Similarly, start an nginx, and at this time share the host network and use it according to the situation. In this way, there is no need to do port forwarding, and the network transmission efficiency will be higher (think about why). |
>>: Working principles of physical layer/data link layer/network layer
Recommend
Serverless Engineering Practice | Tips for Optimizing and Debugging Serverless Applications
Tips for debugging serverless applications During...
Zhang Pingan, President of Huawei Consumer BG Cloud Service: Fertile Soil, Shining Stars, Win-win Digitalization
On June 22, DigiX2018 Huawei Terminal Global Part...
Outlook for domestic 5G development in 2021 (I): Current status
The development of 5G has now become another hot ...
Revelation from global 5G speed test: Can operators break away from homogeneous competition?
The same coverage, the same bandwidth, the same m...
Talk about my operating system and daily application software
operating system Manjaro is a distribution based ...
5 reasons why DevOps will be a big thing in 2018
DevOps has been a hot topic for a few years now. ...
Why are operators competing to launch new 4G packages as 5G is the mainstream?
[[406115]] In 2021, when 5G is rapidly popularize...
DesiVPS: Los Angeles 1Gbps unlimited traffic VPS for $22 per year, supports free IP change
DesiVPS has launched the Year End Stock Clearance...
Video and Network - Why is 700MHz the golden channel?
Labs Guide 700M is called the "golden freque...
Sharktech: $129/month-Dual E5-2678v3/64GB/1TB NVMe/1Gbps unlimited traffic/Los Angeles data center
Sharktech's low-priced configurations in Los ...
DiyVM: US CN2/Hong Kong CN2/Japan Osaka VPS monthly payment starts from 50 yuan, Hong Kong server starts from 499 yuan/month
DiyVM is a Chinese hosting company founded in 200...
ExtraVM offers 30% off on Netherlands data center, 1Gbps unlimited traffic VPS starting at $3.5 per month
ExtraVM recently launched a new VPS host in the N...
Driving innovation and unleashing the unlimited potential of fiber optic LAN
It’s no secret that there are hard limits associa...
Review of the top ten 5G trends in 2021: coverage, applications, and a future
Looking back at the communications industry this ...
![[11.11] LOCVPS top up 100 yuan and get 10 yuan, all hosts are 60% off, Hong Kong VPS monthly payment starts from 22 yuan](/upload/images/67cabd32b921f.webp)




![[Black Friday] RAKsmart: San Jose servers start at $30/month, Los Angeles servers start at $60/month, Japan servers start at $99/month](/upload/images/67cac494a247b.webp)